WordPress is the most popular CMS on the planet with a 43.3% share of all websites on the internet. WordPress with its flexibility and plethora of features, themes, and plugins is the go-to choice for bloggers and developers alike. But due to its widespread use, it catches the eyes of cyber threats and attacks.
In February, critical WordPress vulnerabilities struck 9 plugins, affecting 1.3 million websites. I don’t think you need more reasons to understand the importance of securing your WordPress website.
Yes, we can never estimate the number of attacks or threats on our website(s). This does not mean we should not know about them and fortify your website’s defenses before something happens! And if you think that your website and passwords are impenetrable, then have a look at the 200 most common passwords. 🧐
Although the war between good and evil seems endless, but with website security you have a greater chance against malicious activities (for evil better have an exorcist 👻). Most of the WordPress site security issues are related. If you fix one good, it gives an added protection from another issue, and so on.
So, the citizens of WordPress, here is the security threats bulletin, wanted over the globe for disrupting, slowing down, data theft, etc. of wonderful and good-looking websites:
Wanted: Dead or Alive
- Unsanctioned Logins
- Archaic Core Software
- Undefined User Roles
- Prehistoric Plugins and Themes
- Malware
- SQL (Structured Query Language) Injections
- SEO (Search Engine Optimization) Spam
Unsanctioned Logins
This exactly resembles movie scenes where the protagonist or antagonist tries to break into a highly secure facility to steal valuable data. The major focus is on cracking the password, where a computer runs like a matrix and fetches the password. That’s exactly how brute-force attacks work, providing unsanctioned or unauthorized login access to the user.
In this type of attack, a bot is used that runs billions of potential combinations of username-password, and if the hacker(s) get lucky, Voila! your ultra-safe nobody can guess the password has been cracked in an exhaustive time of 2 minutes (not for all cases!). 😵
Insights
- Reaching the default backend page of a WordPress site is quite easy. All you have to do is subjoin /wp-admin or /wp-login.php to the site’s main URL, and you’re at the backend page (Try WPWhiteboard.com/wp-admin, works like a charm right?). It won’t work with WPWhiteboard, ain’t that easy to reach. 🤣
- Landing on the backend page is still a job half done, as cracking the username and password is still a difficult task, but thanks to your password and username choices, it might be a piece of 🎂.
What Should I Do?
You must’ve heard and read this many times, but, once again for the sake of your website and the cyber world, if you think your password is strong, think again, no really, think again!
Let me show you the magic of using lowercase characters (LC), uppercase characters (UC), digits, and special characters (SC) in your passwords. The image below shows the stipulated time to crack a password if an algorithm is guessing the password @ billions per second. 🚀

And if you think, the whole reason behind keeping simple and common passwords is that it makes it easier to remember them, then smarty pants it is the generation of password managers! You can use them to store passwords, just like my web browser does!
You can go beyond this and add another layer of security, with 2FA (Two-factor Authentication). 2FA requires you to provide additional information, mostly logging in on a separate device after filling in your username and password. This makes the website more secure, and impenetrable for at least a thousand years, give or take.
Also, you increase WordPress security by removing account(s) with the “admin” username. If I can write it here, hackers can guess the same. Remember brute force attack is all about cracking passwords, but that does not mean you cannot add a weird and tough username, making attempts to crack your password super tough and near impossible!
Archaic Core Software
An advantage of using WordPress as a CMS and a website-building platform is that it gets regular and over-the-counter updates, making sure that your website runs on the latest technology, and providing a seamless UX with complete security. All you have to do is make sure your core software is up-to-date!
WordPress developers roll out updates every quarter or so, here’s the recent update Misha. Although it’s up to you to use any version of WordPress. If you are nowhere near codes and anecdotes, better check for updates and get it done ASAP! 👨💻
Insights
- WordPress core updates along with providing innovative and useful features also address critical WordPress security threats. Check if your website is running on old software, if yes, I’d suggest you update real quick!
- Also, you make sure that the plugins and theme of your WordPress website are updated and up-to-date with the latest WordPress version. I’ve discussed this in detail below, keep reading…
What Should I Do?
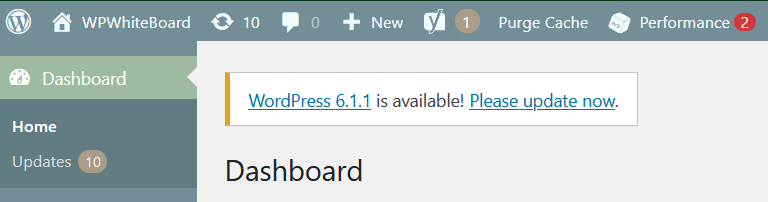
You have to make sure that you stay updated on the latest WP version. WordPress updates to the next version automatically. But, if you have disabled that, you can see the latest update shown on the WordPress dashboard (image below!). To know about the latest releases of WordPress, read here!
ill-Defined User Roles
Each role comes with its default permissions that provide various levels of access to your website. If you want someone to just post on your blog, or someone to just check and respond to comments, etc.
Each role comes with default permissions that authorize or restrict users to take specific actions on your site, like, installing/modifying plugins, publishing content, changing settings, etc. When you create a new user on your WordPress website, the default role given is Administrator. Make sure to change and allocate the roles with caution!
In WordPress, there are four default user roles to choose from:
- Administrator: Have access to all the admin features, basically complete control over a website. 🕹️
- Editor: Can publish and manage thy own posts, along with other posts on the website.
- Author: Publish and manage thy own posts.
- Contributor: Edit and create thy own posts, but cannot publish them.
- Subscriber: Manage, update their own profile, view posts, and write comments.
As WordPress is known for its customization, you can also make custom-defined user roles. Interesting, right? Many plugins offer different user roles. Let’s take the Yoast SEO plugin for example. It comes with two additional user roles:
- SEO Manager: All SEO capabilities, including full access to the Yoast SEO settings, and features.
- SEO Editor: Access to features of Yoast SEO meta box. No access to sidebar settings can make and manage redirects.
Super Admins have access to multi-site and single-site administration features.
Insights
In the case of multiple users, where everyone is admin, it could become a major security concern. So, if anyone has a weak password or has left login credentials somewhere, could bring havoc to your website. No offense or allegations, I’ll just quote Murphy’s law: “Anything that can go wrong will go wrong”.
So, ill-defined admin roles kinda increase the risks to your website. If a brute-force attack is successful, then a hacker gets a VIP pass to your website. Also, XSS (we’ll cover this in detail below) can enable hacker(s) to have front-end capability, and obtain vital information from your site’s visitors.
What Should I Do?
One knot you should tie on your worksheet is to regularly scan all permissions of your website. If you’re the only admin, make sure you use 2fa and create an indestructible password.
If you are assigning roles to other users, make sure to give them the necessary permissions only. Also, no matter what the role is, make sure all your users strengthen their passwords and use 2fa.
Make sure you give necessary permissions to the users of your website. As mishaps can happen, hackers are always waiting for an opportunity. Also, it’s not just about vulnerability to external factors, sometimes, mistakes happen. For eg. a contributor can delete a high-performing post by mistake 😱, owing to less knowledge of WordPress. But, you gave him an admin user role, so, it’s your fault!
Historic Plugins and Themes
WordPress is extremely popular for its flexibility and ease of use. It is owing to the design and development capabilities it offers to both creators and developers. Endless customization options, the ability to design and change every element, etc. are one of the major appeals which pull people to WordPress.
Also, it is a great marketplace with developers and designers creating hundreds of themes and plugins for you to use and build the website you dream of! But, as we read about using old core software can cause WordPress security threats, the same is the case with outdated themes and plugins.
Acc. to WPScan, 97% of vulnerabilities in their database are plugins and themes, while only 3% comes from the core software.
Insights
Most of the plugin and theme developers release functionality enhancements, security fixes, and additional features with frequent updates. But, it does not happen with all the themes and plugins.
Those remaining plugins and themes in use with no updates, often open doors for hackers and leave your site vulnerable. How do you ask? Let’s say there’s a vulnerability related to theme templates and its creation. If your theme is not up-to-date with the latest WordPress version which solves the issue. A hacker can exploit the theme’s vulnerabilities to gain control of your site.
What Should I Do?
Updates improve website security but also increase the overall WordPress experience with many feature additions, fixes, etc. You should monitor for updates and ensure that your website is running on the latest version of themes and plugins, compatible with the latest core software.
When updates are available for plugins and themes, you can install them manually or use a plugin to automatically install them as they go live. So, make sure you regularly check your plugins and themes and update them to the latest version.
Malware
Malware includes any malicious software, thus, taking its name; ‘Mal’+ ‘Ware’. These malicious files can be placed in legitimate files, plant codes in existing files, etc. Hackers use these methods to steal data from websites, their visitors, and wreak havoc on a website.
Example, ZeuS is a modular banking trojan which uses keystroke logging to compromise victim credentials when the user visits a banking website. Since the release of the ZeuS source code in 2011, many other malware variants have adopted parts of its codebase, which means that events classified as ZeuS may actually be other malware using parts of the ZeuS code.
Insights
The threats we discussed in this article are directly related in some way. Malware usually enters through unauthorized and historic themes and plugins. Hackers can take advantage of security issues in themes and plugins, imitate them, or create new add-ons to place harmful codes on your website.
WordPress has a default check in place that restricts the file types for users. If you try to upload a file that isn’t there in the database, an error message occurs, or simply the file will not upload. This step is good as a preventive measure but can be easily bypassed if someone gains access as the administrator.
What Should I Do?
Carefully check the theme and plugins your website uses or planning to use. WP.org lists all valuable stats in their directory, check out the image below:
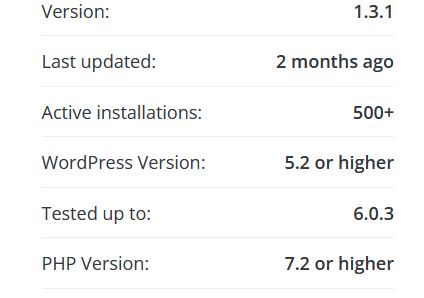
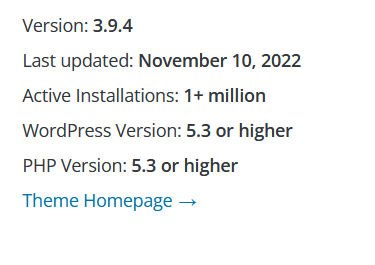
You can check these statistics out on wordpress.org/themes or wordpress.org/plugins. Select a plugin/theme and you’ll find the related stats on the right!
Take an additional step by conducting regular security scans to find any potential issue or malware hiding on your WordPress website. There are many plugins you can use to do this job without any trouble (Don’t worry these are highly rated and extremely secure plugins). For example, Wordfence security, Jetpack, etc.
Structured Query Language (SQL) Injections
SQL is a programming language used to access stored data on a site. It’s the preferred language on WordPress when it comes to database management. It is secure, but there is no stopping malicious intents, right?
An SQL injection enables a hacker to modify your site’s database directly. Attackers can make/modify accounts, and add unauthorized links, content, etc. They can also edit, delete, and leak important data and information on the site.
Insights
WordPress sites are designed to have a broader approach, catering to the community. Attackers often exploit visitor-facing submissions like contact forms, payment fields, lead forms, etc. Hackers use these fields to submit codes that will run and make changes on your site.
What Should I Do?
The best course: Be careful of every user input! As any form submission on your site can be used by attackers to submit information to your SQL database.
You can outsmart attackers by restricting the submission of special characters in visitor form submissions. Without symbols, a malicious code turns into harmless gibberish (Ha-Ha, look who’s laughing now!). You can make use of a form plugin, or security plugin to do this for you. You can also step up the game by having a captcha as the final step before any visitor submission. 😉
Search Engine Optimization (SEO) Spam
SEO spam is similar in nature to SQL injections but is targeted at the most precious asset of your site: SEO. This spam attacks your top-ranking pages and fills them with spam keywords, pop-up ads, etc. to sell fake merchandise.
Insights
These are often caused by: old plugins, themes, and core software. Not only this, brute force attacks and ill-defined user roles can also add to increasing your WordPress site’s vulnerability.
Beware as these hacks are hard to detect, as after hacking attackers wait to not raise any suspicion. Since it is SEO spam, they’re targeted at your top-ranking pages, so you will overlook them when conducting your review and analysis. A simple keyword placement like “cheap Hermes bags”, in between the content of your website, without breaking the original code of the site.
SEO spam is wide open to SEO crawlers, as they’ll index your site for the spammy keywords and users searching for Hermes bags (or whatever the spammy keyword is).
What Should I Do?
First of all, make sure your theme and plugin are updated and compatible with the latest WordPress version. Double-check your user roles and how you have defined each of them. You can also use WordPress security plugins to run security, malware, database scans, etc.
If you wish to take the command in your hands, then keep your eyes like a hawk on the analytics data of your website. Look out for sudden changes in SERP positions, and increased site traffic for no apparent reason.
You may also get notifications from an internet browser about notices featured on your site that aren’t related to it. If you have coding knowledge, you can go through the ranking pages that affects and attempt to identify the misplaced keywords.
Whatever you do, target and address these hacks early on. SEO crawlers will strike these spammy tactics, and in that process, your hard work, your website’s ranking, and your position take a major hit!
Conclusion
Security and Data Privacy+Protection need to be given more priority. Because, honestly speaking, we do not give much importance to it. If you’re new to website security or an old veteran, sometimes, we tend to overlook these details which may lead to bigger problems. So, prevention is the best medicine, always!
Well, here are 7 types of security threats a WordPress website may face. You know what, it doesn’t end here, because we want you to have All-Thing Everything WordPress. So, here’s part 2 of this article covering some more threats and how you can defend against them.
Feel free to drop your comments on some more useful tips and tricks to safeguard your website. And if you’re the shy kind, you can always write to us at hi@wpwhiteboard.com.
Comments