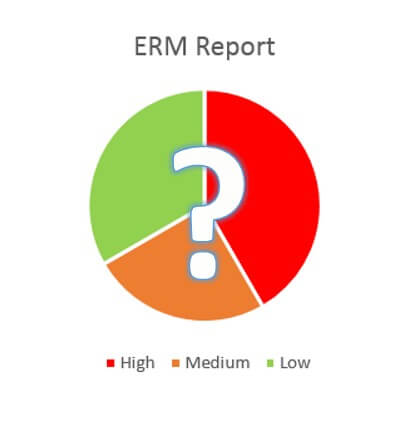
Governance programs are the unsung heroes of 21st-century business operations. Their situation is analogous to that of football’s offensive line.
If an offensive line does its job, no one will notice it, but when something goes wrong, the spotlight shifts.
Governance personnel know this feeling all too well. Unwanted surprises – be they compliance notices, audit findings, or a poor vendor relationships – are bad for business. Even a good surprise, like exceeding a sales target, can cause trouble i